حمله DoS و DDoS چیست و چگونه باعث Down شدن سایت میشود
- امنیت وردپرس
- بروزرسانی شده در
این مقاله به شما کمک میکند تا بتوانید به خوبی آنچه را که در پشت پرده اتفاقات یک سایت است بشناسید. به طور کلی همه سایتها، روی سرورهای مختلفی قرار دارند. این سرورها نوعی رایانه هستند. زمانی که شما آدرس سایتی را در مرورگر خود جستوجو میکنید این رایانهها پس از بررسی درخواست شما، اطلاعات سایت را نمایش میدهد. هر سرور توانایی پشتیبانی از مقدار محدودی درخواست را دارد و زمانی که تعداد موارد ورود به سایت، بیش از حد توان سرور شوند؛ این سرورها از دسترس خارج یا اصطلاحاً down میشوند. با حمله Dos و DDos دقیقا چنین اتفاقی برای سایت شما خواهد افتاد.
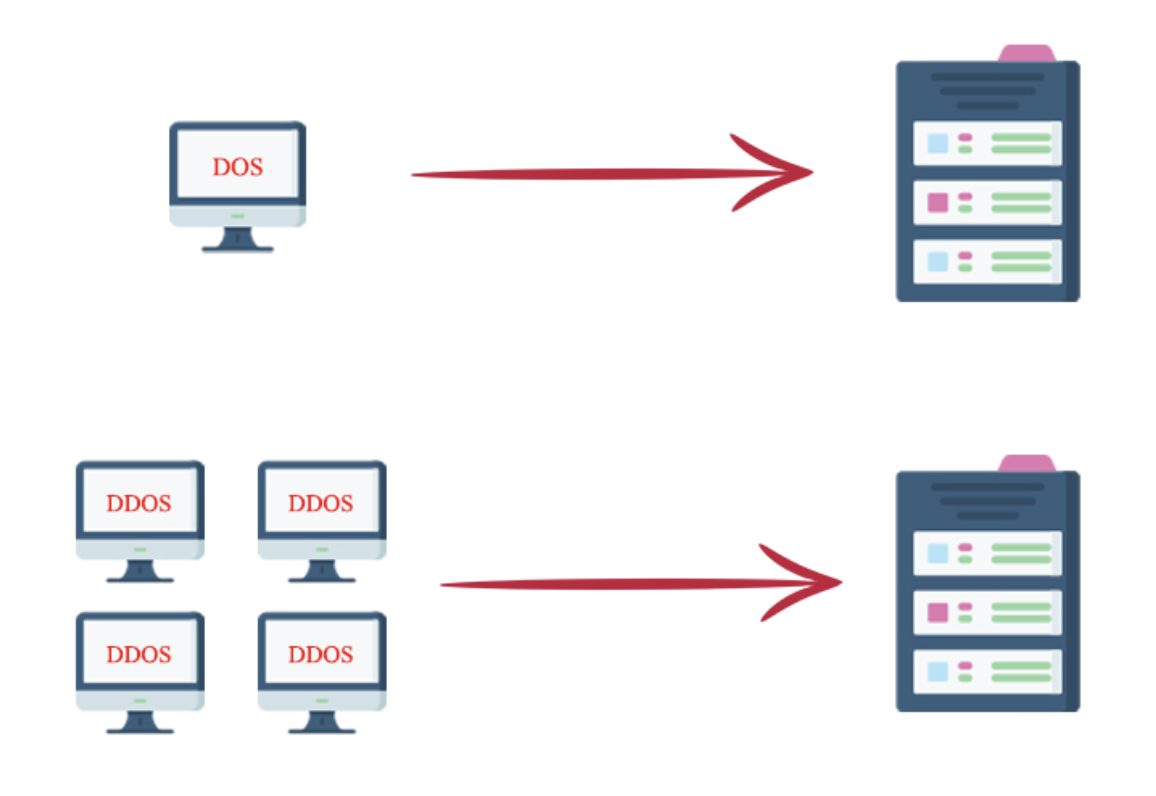
حملات داس (DOS) یا Denial of Service (به معنای محرومسازی از سرویس) از بهروزترین و گاهاً خطرناکترین نوع حملات سایبری هستند. در این نوع حملات هکرها تلاش میکنند با ارسال حجم زیادی از درخواست ورود به سایت شما، مقدار زیادی از منابع سختافزار سایت را مصرف میکند و این حرکت باعث میشود که سرور شما برای مدتی از دسترس خارج شود.
سازوکار اصلی حملات دیداس (DDOS) یا Distributed Denial of Service (به معنای محرومسازی از سرویس توزیع شده) نیز مانند حملات داس است با این تفاوت که حملات داس با یک رایانه انجام میشوند اما حملات دیداس از طریق چند رایانه جداگانه و به طور همزمان صورت میگیرد.
به طور کلی این نوع حملات زمانی اتفاق میافتد که ترافیک غیرعادی روی سایت شما افزایش پیدا کند و مانع دسترسی کاربران، به اطلاعات سرور شما شود. مهاجم با هدف قرار دادن رایانه و اطلاعات آن از دسترسی شما به اکانتها و سایر سرویسهای روی سیستم جلوگیری میکند.
آنچه در این مقاله میخوانید
تفاوت حمله Dos و DDos
باتوجهبه آنچه پیش از این توضیح دادیم، شناخت تفاوتهای این دو حمله ساده است. در حملات دیداس ترافیک از چند سیستم متفاوت به سایت شما منتقل میشود که در واقع ردیابی و دسترسی به فرد حمله کننده را دشوارتر میکند و به نسبت حملات مخربتر و گستردهتری صورت میگیرد. حملات داس اصولاً سادهتر هستند و شما حتی با سیستم شخصی خود نیز میتوانید در ابعاد محدودی سرور مورد نظرتان را مورد حمله قرار دهید.
حمله کننده
هر فرد یا گروه برای انجام این کار میتواند دلیل خود را داشته باشد. اما طبق گزارشهایی که در دسترس است تعدادی از این حملات برای کنار زدن ناجوانمردانه رقبای تجاری صورت میگیرد یا گاهاً افراد برای از بین بردن بعضی محتوای مبتذل یا ضد اجتماعی با این نوع حملات، اینگونه اطلاعات را از دسترس خارج میکنند. البته افرادی هم هستند که با استفاده از این حملات، قصد دارند مدیران سایت را از ایمن نبودن سایت در برابر این حملات آگاه سازند.
نشانه حمله Dos و DDos
زمانی که این حملات اتفاق میافتد اگر شما زود متوجه شوید امکان دارد که تا حدودی بتوانید از بروز خسارات بیشتر جلوگیری کنید. اگر سرعت پاسخگویی سرور شما به طور غیرمنتظرهای کاهش بیابد میتواند از علائم این حملات باشد. اما توجه داشته باشید که گاهی شما این موارد را میبینید ولیکن حمله نیستند بلکه ممکن است هر نوع اختلال یا حتی افزایش کاربر عادی باشد.
مورد بعد عدم اتصال صفحات داینامیک به سرور است در این مواقع معمولاً پیام تکمیل ظرفیت را دریافت خواهید کرد. پیشنهاد میشود در صورت مشاهده این مورد مرورگرها را طوری تنظیم کنید که تا مدتی به سایت شما مراجعه نشود. نشانه بعدی استفاده بیش از حد و غیرعادی از منابع سرور مثل حافظه یا پهنای باند است که اصولاً در مدت زمان کوتاهی اتفاق میافتد.
در ابتدای توضیحات خود، این را مطرح کردیم که حملهکنندهها با ارسال درخواستهای زیاد و غیرمعمول تلاش برای تخریب سرور شما دارند؛ پس اگر تعداد درخواستهای بالا و غیرعادی دریافت کردید، باید بدانید که از نشانههای حملات داس و دیداس است. گاهی این نوع حملات ایمیل یا هر یک از دیگر سرویسها را هدف میدهد و باعث کندی و اختلال در ارسال و دریافت اطلاعات میشود.
روشهای حمله
این حملات روشهای بسیار مختلف و متنوعی دارند که ما چند مورد از آنها را برای شما نام میبریم:
ICMP Flood: در این روش مهاجم با ارسال درخواست یا بستههای ping سیستم هدف را مورد حمله قرار میدهد و باعث اختلال در سرویسدهی میشود. تکرار این کار سرور را کاملاً اشغال کرده و آن را از کار میاندازد.
Teardrop یا Teardrop attacks: حمله کننده در این شیوه، آیپیها را تکهتکه و ناقص ارسال میکند و طبیعتاً این کار سختافزار گیرنده را دچار مشکل میکند. معمولاً سیستمعاملهای قدیمیتر مثل ویندوز 95 در مقابل این حملات آسیب پذیری بیشتری نشان میدهدند.
SYN Flood: در این مورد حمله کننده با ارسال درخواستهایی از نوعTPC/SYN خود را یک کاربر معمولی نشان میدهد. سپس درخواست خود را برای دریافت اطلاعات ارسال میکند و پس از دریافت پاسخ، سرور را باز نگه میدارد. با افزایش این درخواستهای نیمه، سرور اشغال شده و موجب بروز اختلال و در نهایت از کار افتادن سرور مورد نظر میشود.
چگونه از حملات Dos جلوگیری کنیم
در واقع بروز این حملات نقص سرور سایت را نشان میدهد. باید برای جلوگیری از وقوع مشکلات این چنینی از مدیر سرور خود بخواهید تا با استفاده از روشهایی نظیر بروز بودن همیشگی سختافزارها و نرمافزارها، استفاده از برنامههای فایروال در سیستمها و سرورها، نصب ابزارهای امنیتی و… استفاده کند. اگر مدیر سایت بر میزان ترافیک و درخواستهای معمولی سرور آگاه باشد بهمحض دریافت ترافیک یا درخواستهای غیرعادی از وجود حمله مطلع خواهد شد.
بهتر است شما نیز اگر زمانی نشانههایی از حملههای داس و دیداس را مشاهده کردید سریعاً به هاست خود اطلاع دهید تا از خسارات و زیانهای گستردهتر جلوگیری شود. با همه این تلاشها و پیشگیریها گاهی جلوگیری از بروز مشکلات پس از وقوع حمله بسیار دشوار و گاهی ناممکن میشود. جالب است بدانید، سایت محبوب GitHub که تمام برنامهنویسان با آن آشنایی دارند در سال 2018 در معرض بزرگترین حمله DDos قرار گرفت. هکرها توانستند در هر ثانیه تقریباً 130 میلیون بسته ارسال کنند.
مدت زمان حمله
شاید این سؤال برای شما هم پیش بیایید که از آغاز حمله تا پایان آن چقدر زمان میبرد. باید بگویم برای اینگونه مسائل مدت زمان معینی نمیتوان مشخص کرد؛ چرا که به میزان سماجت مهاجم و قدرت مقابله مدافع بستگی دارد. به زبان سادهتر اگر مهاجم به کار خود ادامه دهد و مدافع نیز نتواند به خوبی اوضاع را کنترل کنند و از حمله جلوگیری کنند؛ ممکن است حمله ساعتها طول بکشد. در بهترین و خوشبینانهترین حالت، ظرف مدت کوتاهی (حدود چند دقیقه) به پایان میرسد و در بدترین حالت، ممکن است چندین روز و به طور مرتب این حملات، به طول بیانجامد.

با سلام
ببخشید من حدود یک سال پیش از المنتور استفاده میکردم و بلد بودم که چجوری دکمه هارو در المنتور گرادیانت کنم اما بعدش قالب سایت رو تغییر دادم و با ویژال کامپوزر کار کردم و الان دوباره دارم با المنتور کار میکنم
حالا میخوام دکمه گرادیانت بسازم اما تو قسمت استایل دکمه در المنتور هیچ گزینه ای برای گرادیانت کردن نیست
لطفا کمک و راهنمایی بکنید
بله متاسفانه در نسخه جدیدش این قابلیت رو حذف کرده. امکان قرار دادن پس زمینه تصویری هم ندارید مگر اینکه از div استفاده کنید و به اون لینک بدید.
با سلام تشکر از شما آقای رضا راد
پس شما چجوری برای دکمه های سایتتان گرادیانت میزنید؟ از div استفاده میکنید؟
سلام و تشکر. بله
با سپاس از شما
سلام
یک سوال داشتم ایا میشه سیپنل کرک شده یا دایرکت ادمین یا هرسیستم کنترل پنل هاست دیگه ای رو روی localhost زمپ نصب کرد؟
چون میخوام محیط هاست رو اجرا کنم در کنار وردپرس
سلام بله میتونید
با سلام ممنون ازتون میشه در مقاله بعدی سایتون به این موضوع نصب سی پنل روی لوکال هاست بپردازید !! ممنون میشم فک کنم اگر چنین مقاله و آموزشی رو بزارید اولین سایت هستید که به این موضوع و آموزش میپردازه با سپاس از شما
خواهش میکنم. ما در حوزه نال و نرمافزارهای کرک شده آموزش قرار نمیدیم به همین دلیل نمیتونیم این موضوع رو آموزش بدیم. البته کامپیوتر شما باید لینوکسی باشه برای اینکار.
بازم سپاس از شما مراحل نصبش مثل همان نصب روی هاست واقعی است دیگه درسته؟ البته برای سیستم عامل لینوکس
خواهش میکنم. بله دقیقا
خواهش میکنم. بله دقیقا همینطوره
با سلام خوب هستید؟یک سوال داشتم شما برای ضبط دوره امورشی وردپرس از چه دستگاهیی استفاده کردید که انقدر با کیفیته؟ میکروفون ؟ هدفون؟ چه چیزی؟
با سلام
در دوره آموزش تولید محتوا این مورد به صورت کامل توضیح داده شده است
با سلام نمیدونم امروز چرا یهو از پنل وردپرس پرید بیرون و هرچی ادرس پنل مدیریت وردپرس رو سرچ میکنم ارور میده و میگه با عرض پوزش، شما اجازهٔ دسترسی به این برگه را ندارید. در صورتی که من با اکانت ادمین وارد میشم
با سلام
مشکل از دیتا بیس و سطح دسترسی در هاست شماست. از هاست بخواهید که مشکل را بررسی کنند
با سلام ببخشید گفتم خطای 500 خطای 500 نیست خطای 503 هستش
درود بر شما خطای ۵۰۳ خطای سرویس هست و از سمت هاست شماست.
با سلام
چندروزی هست که سایتم بسیار خطای 500 میده و سی پی یو سرور و هاستمم به شدت بالا میره
در صورتی که سایتم بسیار بهینه و کم حجمش کردم
و زمانی که خطای 500 نمیده در کمترین زمان و ثانیه لود میکنه فک میکنید مشکل چیه؟
در ضمن توی همین یکی دوروز که خطای 500 هم میده ایمیل خودکار سایتم از کار افتاده و درست نمیشه یعنی به هاستم خوب متصل نمیشه چند بار هم چکش کردم و … اما نشد
مشکل ایمیل مربوط به این مشکل نیست و. از هاست باید پیگیری کنید.
درود بر شما افزونه query monitor رو نصب بفرمایید. سپس تست کنید ببینید چه افزونه ای بیشترین منابع رو مصرف میکنه.
با سپاس اقای رضا راد تشکر میکنم😊
سپاس از لطف شما
ممنون از شما مشکل رو رفع کردم بخاطر افزونه های زیادی بود که روی وردپرس نص شده بود تقریبا 31 افزونه داشتم
خواهش میکنم.
سلام
ربطی نداره به تعداد افزونه ها
ما روی سایتمون 60 تا افزونه فعال داریم که همشون رو بهینه کردیم و سایتمون توی 2 ثانیه لود میشه
البته با کش که زیر یک ثانیه لود میشه !
و با اینکه هاستمون یه هاست معمولیه ولی بازم فشاری بهش وارد نمیشه
ببینید تعداد افزونه ها مشکل ساز نمیشه معمولا , اغلب در این خطاها یک یا چند افزونه هست که منابع رو مصرف میکنه به علت کد نویسی بد !
ممنون از میهن وردپرس 🙂
بستگی به افزونههای نصب شده داره. همین کدنویسی غیر استانداردی که میفرمایید.
ســـــلام ، خسته نباشید
بیشتر در مورد مقابله با حمله توضیح بدهید 🌹🌹
باسلام
حتما به زودی بصورت ویدیو به همین صفحه اضافه خواهیم کرد
با در دست تعمیر کردن سریع سایت، میشه خسارات رو به حداقل رسوند